With the rise of security attacks and vulnerabilities, every software architect should focus on security considerations for the system under consideration. This article highlights the top 10 things to know about security as a software architect.
#1 – OWASP Top 10 Web Application Security Risks & Secure Coding Practices
- The Open Web Application Security Project (OWASP) is a community providing freely-available articles, methodologies, documentation, tools, and technologies for web application security.
- Key document is OWASP Top 10 Risks for Web Application Security. Click here to read the 2021 version.
- Other useful tools from the OWASP community are:
- OWASP Cheat Sheet Series – Few key cheat sheets are Docker Security, AJAX Security, REST Security, Threat Modeling, Logging, Denial of Service, Multifactor Authentication, and CSRF.
- OWASP Application Security Verification Standard – for testing web application technical security controls.

Secure Coding Practices
- Shift-left security strategy recommends moving security closer to the development process. OWASP Secure Coding Practices is a good guide to start educating the development team about the same.
- As an architect, refer to below security tactics mentioned in Software Architecture in Practice book:
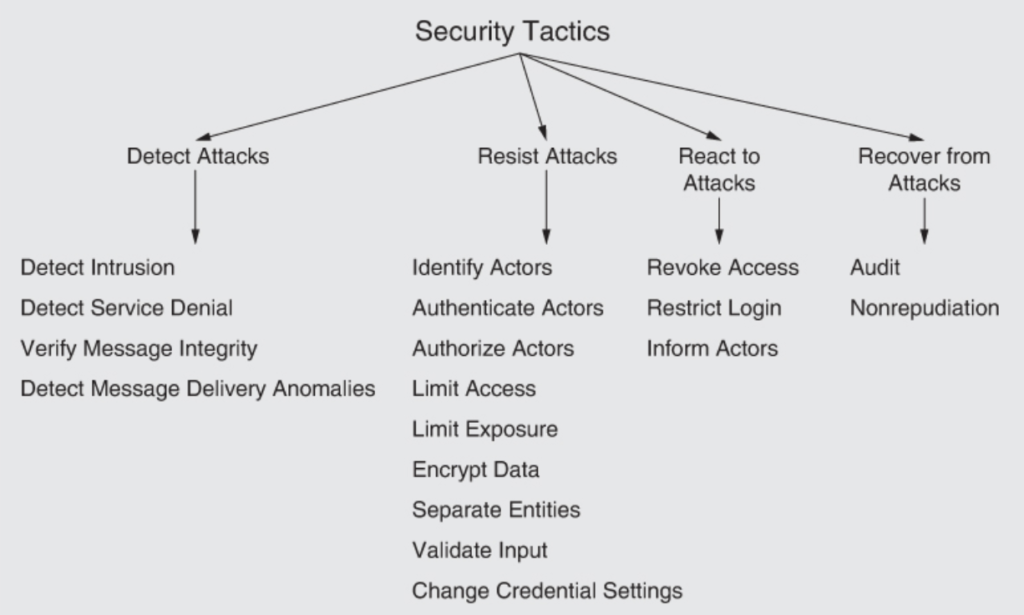
#2 – Security Principles
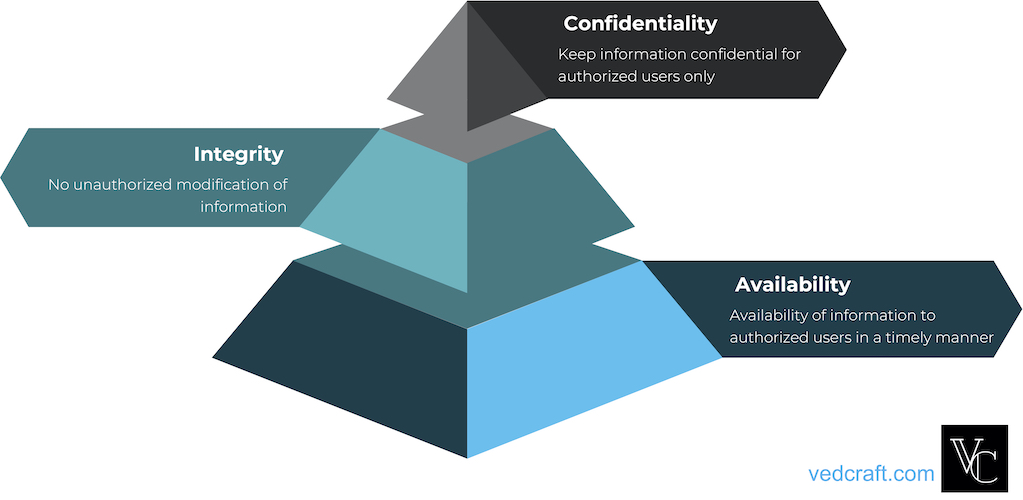
3 basic security tenets on which Security Principles are based are Confidentiality, Integrity, and Availability. CIA triad is a well-known model in the area of information security:
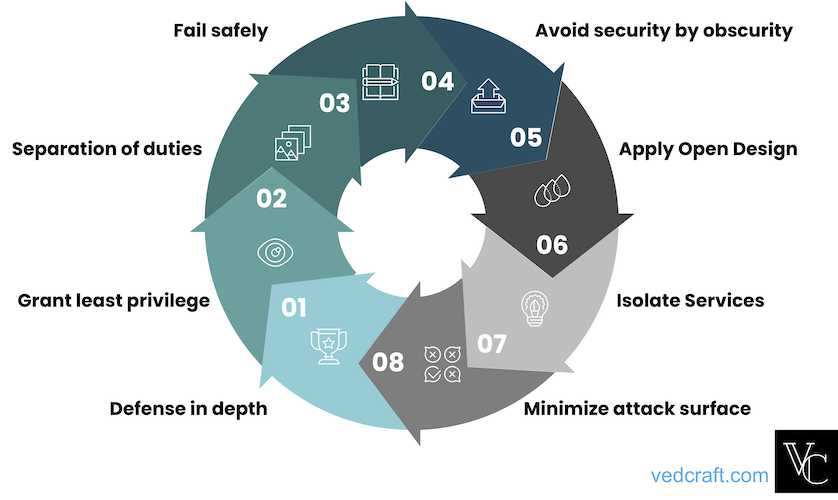
Key Security Principles
- Defense in depth – multiple layers of security control in the architecture
- Grant least privileges – minimum amount of privileges required to perform a specific action or task
- Separation of duties – no user should be given enough privileges to misuse the system on their own
- Fail safely – A mode of termination of system functions that prevents damage
- Avoid security by obscurity – reliance in security engineering on design or implementation secrecy as the main method of providing security to a system or component
- Apply Open Design – design the system in such a way that even it is opensource, it is secure
- Isolate services – unique account should be used for service in order to isolate
- Minimize attack surface – limiting the application areas to be attacked by removing access or similar means
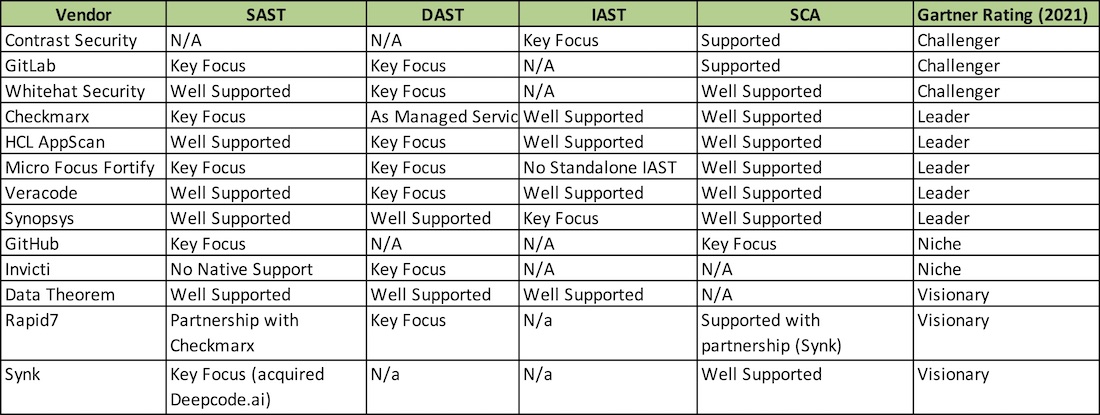
#3 – Application Security Testing
- Software Composition Analysis (SCA) Tools – It is getting popular to detect open source and third-party components in applications and track their known security vulnerabilities and licenses.
- Source code analysis or Static Application Security Testing (SAST) Tools – Click here to see the list of tools (commerical and free) compiled by OWASP.
- Web Application Vulnerability Analysis or Dynamic Application Security Testing (DAST) Tools – Click here to see the list of tools (commercial and free) compiled by OWASP. Dynamic application security testing (DAST) is a process of testing an application or software product in an operating state.
- Interactive AST (IAST) Tools– An emerging technology combining elements of DAST simultaneously with instrumentation of the application under test.
#4 – Cybersecurity Risk Rating Platforms
- Cybersecurity risk rating (CSR) platform is an upcoming trend, which provides a centralized place to get insights associated with risks related to IT infrastructure and third-party ecosystem.
- The concept is similar to the credit rating market to provide a Security Score based on data collected from public and private sources.
- The most common scenarios are to include cybersecurity & continuous monitoring of third-party risks management (TPRM), enterprise security risk management, executive view of security, and benchmarking.
- Key vendors: SecurityScorecard, Bitsight, Panorays, RiskRecon, UpGuard, Prevalent, Black Kite.
#5 – Cloud Security
The below section enlists key security practices & tools available by key cloud service providers:
AWS (Amazon Web Services)
- AWS Security Reference Architecture – provides a holistic view of security services with guidelines.
- AWS Security Services – provides a single view of all the services across identity & access management, infrastructure & data protection, incident response, and compliance.
- AWS Security Hub – provides unified view of security and categorized as a cloud security posture management service that automates best practice checks, aggregates alerts, and supports automated remediation.
Azure
- Microsoft Cybersecurity Reference Architectures – consolidated list of all Cybersecurity capabilities by Azure.
- Azure Security Services – list of all Azure services related to security-related services and technologies.
- Azure Security Center – provides unified capability for security posture management for your multicloud and hybrid environments.
Google Cloud
- Google Cloud Security Practices – as part of Google’s Cloud Architecture Framework covering security aspects.
- Google Cloud Security Solutions – enlists Google’s security services and solutions across the spectrum.
- Google Security Command Center – provides a centralized security and risk management platform.
#6 – Zero Trust Security
- Zero-trust security (aka perimeterless security) is the new way of thinking security in modern architecture with 4 pillars in mind – people, devices, network & workloads.
- Zero Trust Network – The ideology is to focus not only on traffic flowing from “North-South” (traditional model from load balancer -> application layer -> services layer) to “East-West” traffic (new pattern emerging in Cloud where traffic flows sideways between components). Zero Trust Network Access (ZTNA) is a category of technologies that provides secure remote access to applications and services based on defined access control policies.
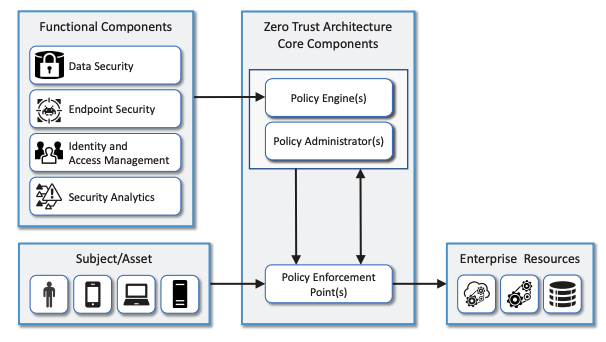
- Zero Trust Architecture (ZTA) – Zero trust is a cybersecurity strategy that focuses on moving network defenses from wide, static network perimeters to focusing more narrowly on dynamic and risk-based access control to enterprise resources (definition by NCCOE). See the architecture components in the diagram below.
#7 – DevSecOps
- DevSecOps —short for development, security, and operations—automates the integration of security at every phase of the software development lifecycle, from initial design through integration, testing, deployment, and software delivery. It is based on a “shift-left” strategy to detect security issues early in the case.
- Security Testing Tools are investing in DevSecOps to automate security testing as part of an automated pipeline particularly for Cloud-native applications.
- DevSecOps Pipeline – a pipeline visualization presented below by JFrog:

- Server hardening – it is the process of configuring setting after base OS has been installed to increase server’s attach surface and increases confidence being server as a secured components. This can also be integrated with DevSecOps pipeline.
#8 – Security Communities & Standards
- Security communities and databases help awareness of industry standards related to security.
- Key communities and standards:
- ISO Standards – Not just limited to security providing widely accepted standards such as ISO/IEC 27001 (Information Security Management).
- OWASP Community – as mentioned in point#1, for web application security.
- OpenSSF – community by the Linux Foundation to improve the security of open source software (OSS).
- NIST Cybersecurity Framework – provides a set of desired cybersecurity activities and outcomes using common language that is easy to understand.
- SANS – provides Cybersecurity trainings, certifications, resources and more as a community.
- Center for Information Security (CIS) – globally recognized best practices for securing IT systems and data.
- The PCI Security Standards Council (PCI SSC) – is a global forum that brings together payments industry stakeholders to develop and drive adoption of data security standards and resources for safe payments worldwide.
- Key repositories:
- NVD Database – U.S. government repository of standards based vulnerability management data represented using the Security Content Automation Protocol (SCAP).
- CVE – with a mission to identify, define, and catalog publicly disclosed cybersecurity vulnerabilities.
- NIST NCP – publicly available security checklist providing detailed low level guidance on setting the security configuration of operating systems and applications.
- Key websites to remain updated:
- Secure Reading Website for Cybersecurity news & updates.
- DevSecOps – founded by Security Practitioners dedicated to the science of how to incorporate security within Agile and DevOps practices.
#9 – Data Privacy
- Data Privacy is the protection of personal data (also known as PII – Personal Identifiable Information) and with rising data breaches, it is one of the most focused area by companies (with legal & compliance obligations).
- General Data Protection Regulation (GDPR) and California Consumer Privacy Act (CCPA) are key regulations providing the frameworks for organizations for compliance.
- Rise of first-party cookie (phasing out third-party cookies) is a recent example of impact data privacy can create on the overall technology solution related to security and beyond. First-party data management strategy is now an essential part of enterprise architecture strategy.
- Cookies Policy by European union is a great example on how you need to provide information on data being captured as part of cookies in the respective website.
#10 – Security Regulations & Compliance
- ISO/IEC 27001 (Information Security Management) – is the international standard for information security and is required to formalize and improve business processes with respect to information security and privacy.
- The Payment Card Industry Data Security Standard (PCI DSS) – is required for applications handling cardholder data, whether you are a start-up or a global enterprise managed by The PCI Security Standards Council (PCI SSC).
- General Data Protection Regulation (GDPR) and California Consumer Privacy Act (CCPA) for data privacy.
References
- Cybersecurity Risks Rating Platforms (Q1 2021) by Forrester
- OWASP Foundation
- Gartner Application Security Testing Tools Overview
- National Cybersecurity Center of Excellence
- DevSecOps Website
- 7 Application Security Principles You Need to Know
- What is Data Privacy?
- How To Target Your Audience Without Third-Party Cookie Data – Gartner


